43 releases (4 breaking)
| 0.5.5 | May 11, 2023 |
|---|---|
| 0.5.3 | Apr 18, 2023 |
| 0.4.9 | Apr 13, 2023 |
| 0.4.1 | Mar 31, 2023 |
| 0.1.9 | Mar 3, 2023 |
#415 in Filesystem
4.5MB
1.5K
SLoC
pathbuster
A path-normalization pentesting tool
Whats New • Bug Fixes • Installation • Usage • Examples • Contributing • License • Join Discord
What's New?
- Removed redundant --filter-status which filtered the status codes but also missed a ton of valid findings.
- Removed redundant --filter-body-size which filtered the response sizes but also missed a ton of valid findings.
- Implemented --drop-after-fail which will ignore requests with the same response code multiple times in a row.
- Added in a --proxy argument, so you can now perform proxy-related tasks such as sending everything to burp.
- Pathbuster will now give you an eta on when the tool will finish processing all jobs.
- Added in a --skip-brute argument, so you have the choice to perform a directory brute force or not.
- Replaced --match-status with --pub-status and --int-status so we have more control over the detection stage.
- Added in a --skip-validation argument which is used to bypass known protected endpoints using traversals.
- Added in a --header argument which is used to add in additonal headers into each request.
Bug fixes?
- Fixed a bug with the ETA, it would not produce the correct results.
- Fixed a bug with the --proxy argument as well as some other small bugs.
- Fixed a ton of performance issues and included directory bruteforcing at the end.
- Massive performance and accuracy increases using itertools instead of double for loops reducing O(n^2) time complexity.
Installation
Install rust
curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh
Install pathbuster
cargo install pathbuster
Usage
pathbuster -h
This command will show the tool's help information and present a list of all the switches that are available.
USAGE:
pathbuster [OPTIONS] --urls <urls> --payloads <payloads> --wordlist <wordlist>
OPTIONS:
-u, --urls <urls>
the url you would like to test
-r, --rate <rate>
Maximum in-flight requests per second
[default: 1000]
--skip-brute
skip the directory bruteforcing stage
--drop-after-fail <drop-after-fail>
ignore requests with the same response code multiple times in a row
[default: 302,301]
--int-status <int-status>
the internal web root status
[default: 404,500]
--pub-status <pub-status>
the public web root status
[default: 400]
-p, --proxy <proxy>
http proxy to use (eg http://127.0.0.1:8080)
-s, --skip-validation
this is used to bypass known protected endpoints using traversals
-c, --concurrency <concurrency>
The amount of concurrent requests
[default: 1000]
--timeout <timeout>
The delay between each request
[default: 10]
--header <header>
The header to insert into each request
[default: ]
-w, --workers <workers>
The amount of workers
[default: 10]
--payloads <payloads>
the file containing the traversal payloads
[default: ./payloads/traversals.txt]
--wordlist <wordlist>
the file containing the wordlist used for directory bruteforcing
[default: ./wordlists/wordlist.txt]
-o, --out <out>
The output file
-h, --help
Print help information
-V, --version
Print version information
Flags
| Flag | Description |
|---|---|
| --urls | the file containing the urls to test make sure it contains a path |
| --payloads | file containing the payloads to test |
| --int-status | used to match the status codes for identifying the internal web root |
| --pub-status | used to match the status codes for identifying broken path normalization |
| --drop-after-fail | specify a status code to ignore if it reoccurs more than 5 times in a row |
| --rate | used set the maximum in-flight requests per second |
| --workers | number of workers to process the jobs |
| --timeout | the delay between each request |
| --concurrency | number of threads to be used for processing |
| --wordlist | the wordlist used for directory bruteforcing |
| --proxy | http proxy to use (eg http://127.0.0.1:8080) |
| --header | The header to insert into each request |
| --skip-brute | use to skip the directory brute forcing stage |
| --skip-validation | this is used to bypass known protected endpoints using traversals |
| --out | save output to a file |
| --help | prints help information |
| --version | prints version information |
Examples
Usage:
$ pathbuster --urls crawls.txt --payloads traversals.txt --wordlist wordlist.txt -o output.txt
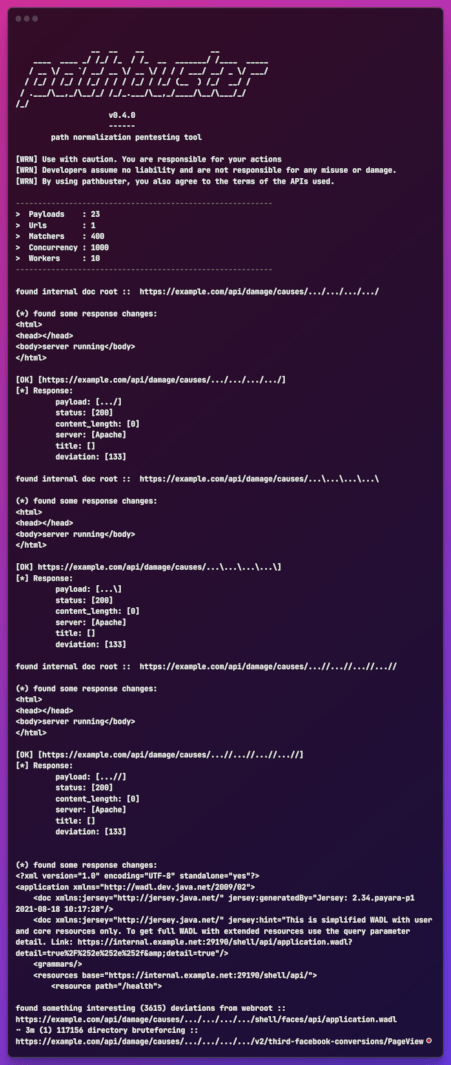
If you find any cool bugs, it would be nice if I have some sorta appreciation such as shouting me out on your Twitter, buying me a coffee or donating to my Paypal.
I hope you enjoy
Contributing
Pull requests are welcome. For major changes, please open an issue first to discuss what you would like to change.
Please make sure to update tests as appropriate.
License
Pathbuster is distributed under MIT License
Dependencies
~14–27MB
~399K SLoC
