6 releases (breaking)
| 0.6.0 | Dec 16, 2024 |
|---|---|
| 0.5.0 | Nov 8, 2024 |
| 0.4.0 | Oct 23, 2024 |
| 0.3.0 | Oct 17, 2024 |
| 0.1.0 | Oct 13, 2024 |
#5 in #br
696 downloads per month
1MB
252 lines

🛢️ 🖥️ Command Line Tools to check for SQL Injection vulnerability. This tool is to help pentest in their daily lives quickly.
Installing
Cargo
Installing from crates.io (requires Rust/Cargo):
cargo install injectsql
Homebrew
You can install with Homebrew:
brew tap heroesofcode/taps
brew install heroesofcode/taps/injectsql
Usage
injectsql
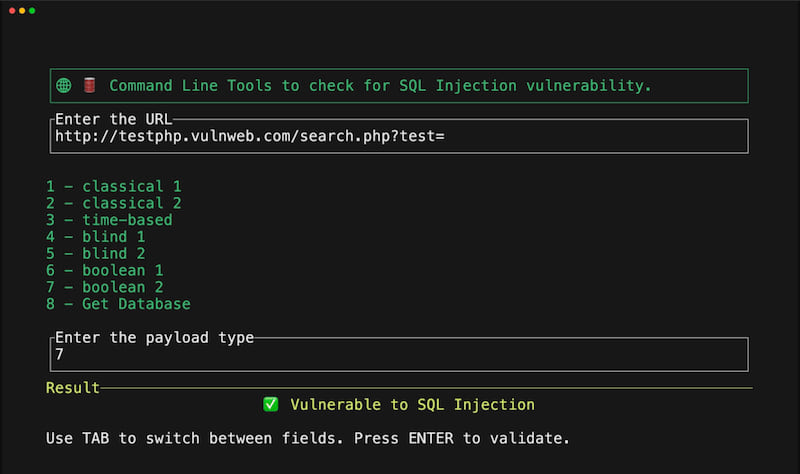
If you want to test or are studying pentest I recommend you use these tools below:
- Acunetix 🇬🇧
- HackTheBox 🇬🇧
- Solyd 🇧🇷
[!IMPORTANT] injeqtor does not perform an in-depth SQL injection attack, it only checks whether SQL Injection is vulnerable and tries to find the name of the database. If you want to carry out an attack to obtain more information, I recommend using sqlmap.
[!WARNING] The use of the
injectsqltool for offensive activities without express permission from the parties involved is illegal. The user is solely responsible for ensuring compliance with applicable local, state and federal laws. The creators of this software are not responsible for any misuse or damages resulting from the use of this program.
Contributing
To contribute, just fork this project and then open a pull request, feel free to contribute, bring ideas and raise any problem in the issue tab.
License
injeqtor is released under the MIT license. See LICENSE for details.
Dependencies
~18–33MB
~509K SLoC