7 releases
| 0.13.3 | Feb 19, 2025 |
|---|---|
| 0.13.2 | Oct 21, 2024 |
| 0.13.1 | Sep 23, 2024 |
| 0.13.0 | May 13, 2024 |
| 0.9.1 | Feb 8, 2024 |
#952 in Parser implementations
Used in dfir-toolkit
88KB
2K
SLoC
Prefetch Parser
A pure rust parser implementation of the windows prefetch. Works on all platforms.
use forensic_rs::prelude::*;
use frnsc_prefetch::prelude::*;
let mut fs = ChRootFileSystem::new("./artifacts/17", Box::new(StdVirtualFS::new()));
let prefetch_list : <PrefetchFile> = read_prefetch_form_fs(&mut fs).expect("Must read all prefetch from filesystem");
Into Timeline
A PrefetchFile structure can be converted into TimelineData be carefull as a single prefetch can be larger than 45Kb and in the process some data is lost like the MFT file references or the file traces.
{
time: 06-11-2023 14:18:00.429,
artifact: Unknown,
fields: {
"artifact.host": "",
"artifact.name": "Unknown",
"artifact.tenant": "",
"file.accessed": 06-11-2023 14:18:00.429,
"file.path": "POWERSHELL.EXE",
"pe.imports": ["\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\WINDOWS\\SYSTEM32\\NTDLL.DLL", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\WINDOWS\\SYSTEM32\\WOW64.DLL", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\WINDOWS\\SYSTEM32\\WOW64WIN.DLL", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\WINDOWS\\SYSTEM32\\KERNEL32.DLL", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\WINDOWS\\SYSWOW64\\KERNEL32.DLL", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\WINDOWS\\SYSTEM32\\USER32.DLL", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\WINDOWS\\SYSTEM32\\WOW64CPU.DLL", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\WINDOWS\\SYSWOW64\\NTDLL.DLL", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\WINDOWS\\SYSWOW64\\WINDOWSPOWERSHELL\\V1.0\\POWERSHELL.EXE", "..."], "prefetch.execution_times": 2945,
"prefetch.version": 30,
"prefetch.volume_files": ["\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\$EXTEND", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\PROGRAM FILES", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\PROGRAM FILES\\SECRMM", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\PROGRAM FILES\\SECRMM\\ADMINUTILS", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\PROGRAM FILES\\SECRMM\\ADMINUTILS\\SDK", "\\VOLUME{01d98a6b8e4b1a36-1c2ea44d}\\PROGRAMDATA", "..."]
}
},
time_context: Accessed
}
let mut fs = StdVirtualFS::new();
let file = fs.open(Path::new(
"./artifacts/30/C/Windows/Prefetch/POWERSHELL.EXE-AE8EDC9B.pf",
)).unwrap();
let pref = read_prefetch_file_compressed("POWERSHELL.EXE-AE8EDC9B.pf", file).unwrap();
let mut forensic_data = pref.timeline();
let event : TimelineData = forensic_data.next().unwrap();
Into Activity
Transforms a prefetch data into a user activity event in order to know which program the user executed.
ForensicActivity { timestamp: 06-11-2023 15:18:00.237, user: "WARD", session_id: Unknown, activity: ProgramExecution(\VOLUME{01d98a6b9e4a0a35-1c9e547d}\WINDOWS\SYSWOW64\WINDOWSPOWERSHELL\V1.0\POWERSHELL.EXE) }
let mut fs = StdVirtualFS::new();
let file = fs.open(Path::new(
"./artifacts/30/C/Windows/Prefetch/POWERSHELL.EXE-AE8EDC9B.pf",
)).unwrap();
let pref = read_prefetch_file_compressed("POWERSHELL.EXE-AE8EDC9B.pf", file).unwrap();
let mut forensic_data = pref.activity();
let activity : ForensicActivity = forensic_data.next().unwrap();
Prefetch Format
The references can be found here: libscca
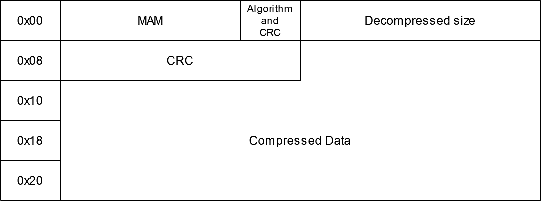
The file format when it's compressed has a MAM signature, followed by the compression algorithm a flag that indicates if it has CRC, the decompressed size, the CRC value and finally the compressed size:
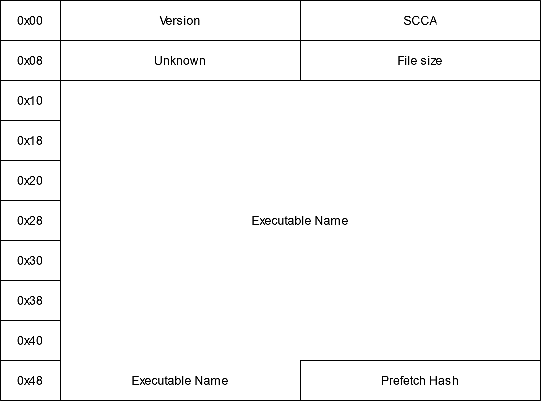
The decompressed file (or the full file when its not compressed) has a header:
- version: The SCCA version used to generate the prefetch.+
- 17: Windows XP
- 23: Windows 7
- 26: Windows 8.1
- 30: Windows 10
- signature: The signature is "SCCA"
- File Size: The prefetch file size
- Executable name: Name of the executable for which this prefetch was created
- Hash: the prefetch hash. Must be the same as the one in the prefetch file name.
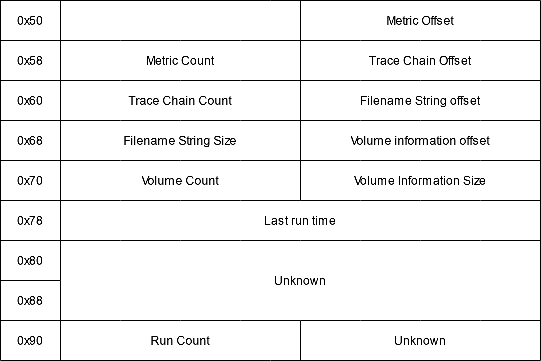
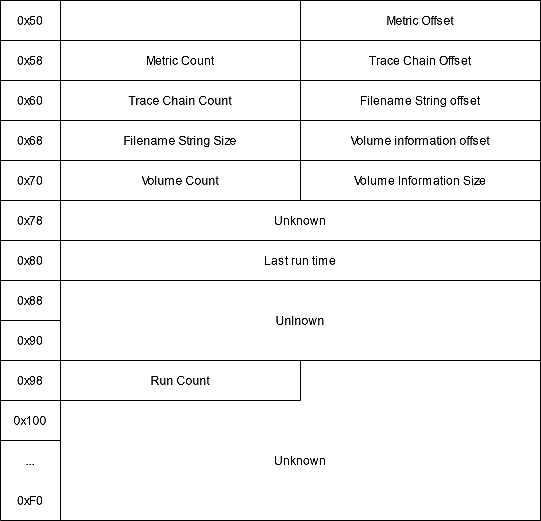
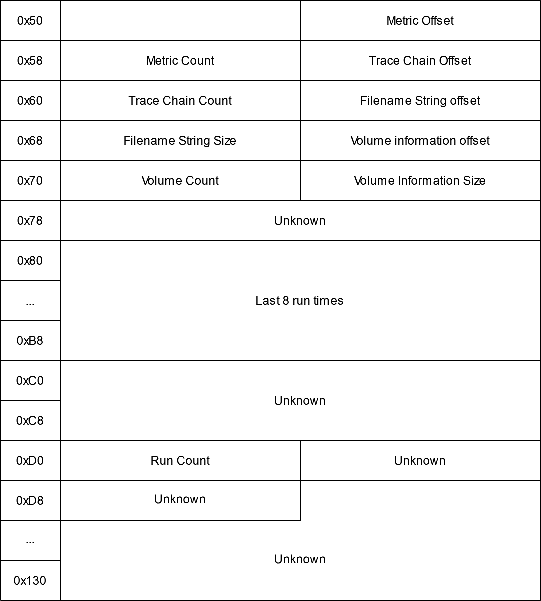
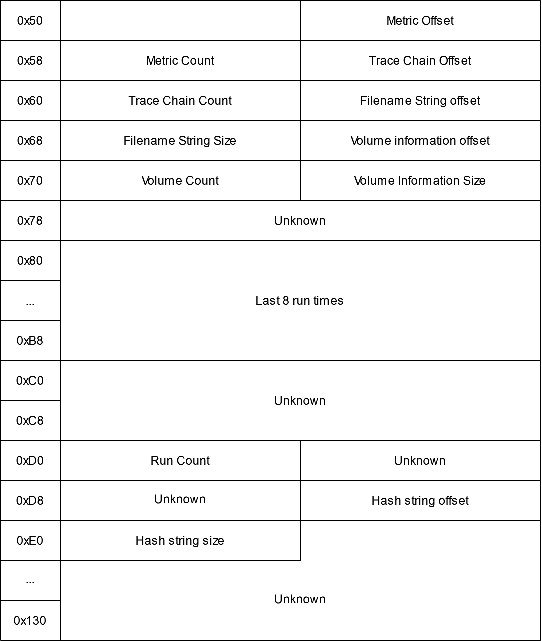
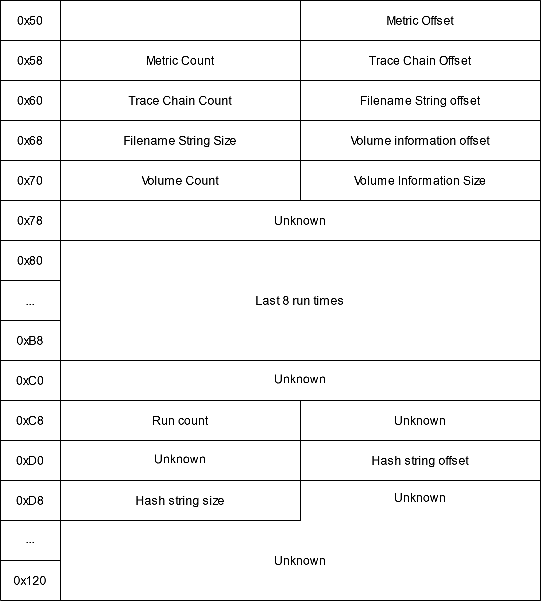
After the header comes version-dependent file information data:
- Positions of the metric data: used to know which DLLs/EXEs loaded the executable.
- Positions of the trace chain
- Location of the strings array
- Location of the volume information array
- Number of executions
- Last execution time: in FILETIME format. For modern versions the last 8 times are stored.
Dependencies
~405–640KB
~13K SLoC