9 releases
| 0.1.8 | Mar 12, 2025 |
|---|---|
| 0.1.7 | Mar 10, 2025 |
| 0.1.6 | Nov 6, 2024 |
| 0.1.5 | Oct 1, 2024 |
| 0.1.0 | Jan 20, 2023 |
#164 in Testing
623 downloads per month
43KB
1K
SLoC
Security Orchestrator CLI

The Product Security Engineering Team's Security Orchestrator also offers a Command Line Interface option for instances where teams have not yet adopted Github Actions, are not using Jenkins, or want to test out the functionality locally. The CLI tool can be installed via Rust.
Quick Start Guide
- Install Rust.
- To install execute the following command:
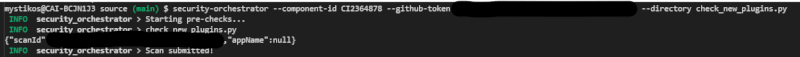
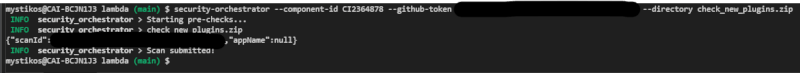
cargo install security-orchestrator - Once the Security Orchestrator has been installed, execute the following command to submit code for scans:
security-orchestrator --application-name --component-id CI123121 --github-token github_token_example --directory 'file or folder path'
Inputs
- Either:
- Component ID (Preferred Option):
--component-id - Application Name:
--application-name
- Component ID (Preferred Option):
- Token:
--github-token - Application Code or Artifact:
--directory- Valid Formats:
- Directory (of source code)
- Binary
- Existing .zip
- Valid Formats:
- Optional Parameters:
--polling: If you pass--polling truethe CLI will wait for results from the scans to come back. You can always cancel the polling withCTRL + C.--scan-id: After you submit a scan the Security Orchestrator will give you back a Scan ID. Pass this Scan ID like so--scan-id {scan-id}to get the results of your scan. If you pass this parameter this will be the only thing the CLI tool looks at. You must remove it if you want to submit a scan.
Examples
Single File
ZIP
Dependencies
~95MB
~2.5M SLoC