4 releases (2 stable)
| 1.0.1 | Jul 19, 2021 |
|---|---|
| 1.0.0 | Jul 15, 2021 |
| 0.1.0 | Jul 6, 2021 |
| 0.0.1 | Jul 4, 2021 |
#8 in #bug-bounty
30KB
1K
SLoC
ppfuzz
Prototype Pollution Fuzzer
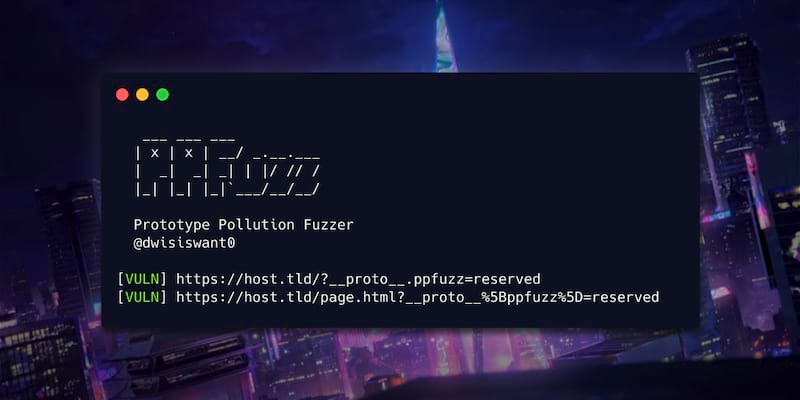
A fast tool to scan client-side prototype pollution vulnerability written in Rust. 🦀
- Installation
- Demonstration
- Usage
- Usage
- Supporting Materials
- Contributing
- Attribution
- Acknowledments
- License
Installation
Binary
Simply, download a pre-built binary from releases page and run!
Source
| NOTE: Rust should be installed! |
Using cargo:
▶ cargo install ppfuzz
— or
Manual building executable from source code:
▶ git clone https://github.com/dwisiswant0/ppfuzz
▶ cd ppfuzz && cargo build --release
# binary file located at target/release/ppfuzz
Dependencies
ppfuzz uses chromiumoxide, which requires Chrome or Chromium browser to be installed.
If the CHROME environment variable is set, then it'll use it as the default executable. Otherwise, the filenames google-chrome-stable, chromium, chromium-browser, chrome and chrome-browser are searched for in standard places. If that fails, /Applications/Google Chrome.app/... (on MacOS) or the registry (on Windows) is consulted.
Demonstration

As you can see in the demo above (click to view in high-quality), ppfuzz attempts to check for prototype-pollution vulnerabilities by adding an object & pointer queries, if it's indeed vulnerable: it'll fingerprinting the script gadgets used and then display additional payload info that could potentially escalate its impact to XSS, bypass or cookie injection.
Usage
It's fairly simple to use ppfuzz!
▶ ppfuzz -l FILE [OPTIONS]
Basic
Use -l/--list to provide input list:
▶ ppfuzz -l FILE
You can also provide the list using I/O redirection:
▶ ppfuzz < FILE
— or chain it from another command output:
▶ cat FILE | ppfuzz
Only show vulnerable targets/suppress an errors:
▶ ppfuzz -l FILE 2>/dev/null
Options
Here are all the options it supports:
▶ ppfuzz -h
| Flag | Description | Default value |
|---|---|---|
| -l, --list | List of target URLs | |
| -c, --concurrency | Set the concurrency level | 5 |
| -t, --timeout | Max. time allowed for connection (s) | 30 |
| -h, --help | Prints help information | |
| -V, --version | Prints version information |
Supporting Materials
- Nuclei templates
- PPScan
- Prototype Pollution and useful Script Gadgets
- JavaScript prototype pollution attack in NodeJS
- Prototype pollution – and bypassing client-side HTML sanitizers
Contributing
When I started ppfuzz, I had very little or no knowledge on Rust and I believe there may be a lot of drawbacks/security vulnerabilities. So all contributions are welcome, of course — any bug reports & suggestions are appreciated, some environment have not been tested yet.
Attribution
Besides being my learning medium, this tool was created because it was inspired by @R0X4R's tip on how to automate prototype pollution checking using page-fetch.
Cross-compile GitHub workflow inspired by crodjer's sysit.
Acknowledments
Since this tool includes some contributions, I'll publically thank the following users for their helps and resources:
- @mattsse - for his awesome chromiumoxide & mentoring me which helped a lot to quickly adapt Rust!
Fourty2#4842(Discord) - for helpful workaround.- All contributors.
License
ppfuzz is distributed under MIT. See LICENSE.
Dependencies
~19–31MB
~509K SLoC