15 releases
| 0.0.22 | Mar 27, 2025 |
|---|---|
| 0.0.19 | Dec 3, 2024 |
| 0.0.18 | Sep 6, 2024 |
| 0.0.16 | Mar 15, 2024 |
| 0.0.12 | Jul 14, 2023 |
#1942 in Network programming
187 downloads per month
735KB
18K
SLoC
ICANN RDAP CLI
This package consists of the following commands:
- The
rdapcommand is a general-purpose RDAP command line client. - The
rdap-testcommand is a testing tool for RDAP.
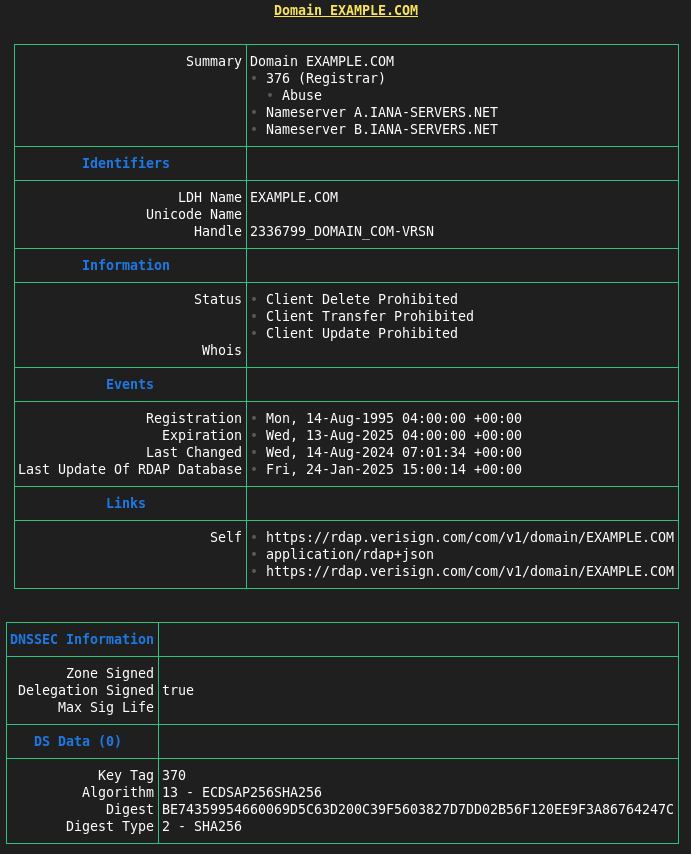
This is a command-line interface (CLI) client for the Registration Data Access Protocol (RDAP) written and sponsored by the Internet Corporation for Assigned Names and Numbers (ICANN). RDAP is standard of the IETF, and extensions to RDAP are a current work activity of the IETF's REGEXT working group. More information on ICANN's role in RDAP can be found here. General information on RDAP can be found here.
Installation and Usage
See the project wiki for information on installation and usage of this software.
License
Licensed under either of
- Apache License, Version 2.0 (LICENSE-APACHE or http://www.apache.org/licenses/LICENSE-2.0)
- MIT license (LICENSE-MIT or http://opensource.org/licenses/MIT) at your option.
Contribution
Unless you explicitly state otherwise, any contribution, as defined in the Apache-2.0 license, intentionally submitted for inclusion in the work by you, as defined in the Apache-2.0 license, shall be dual licensed pursuant to the Apache License, Version 2.0 or the MIT License referenced as above, at ICANN’s option, without any additional terms or conditions.
Dependencies
~26–46MB
~687K SLoC