7 releases
| 0.2.0-beta.2 | Apr 29, 2022 |
|---|---|
| 0.2.0-beta.1 | Apr 22, 2022 |
| 0.2.0-beta.0 | Mar 2, 2022 |
| 0.1.3 | Sep 30, 2020 |
| 0.1.1 | Nov 12, 2019 |
#2278 in Cryptography
34 downloads per month
Used in irmaseal-cli
51KB
1K
SLoC
⚠️ Warning: This implementation has not been audited. Use at your own risk!
PostGuard is an Identity-Based Encryption (IBE) service that can be used to encrypt messages. In Identity-Based Encryption, anyone can encrypt messages for one another. Instead of a public key, the sender only requires the master public key and an identity of the recipient. In order to decrypt, the receiver proves against a Private Key Generator (PKG) - a trusted third party - that he is indeed the correct recipient. Upon succesfully doing so, the receiver obtains a key that can be used to decrypt the message.
About this repository
The repository consists of a workspace with four members:
| crate/package | description |
|---|---|
pg-core |
The core library. The core library's functionality includes:
|
pg-pkg |
An HTTP API server written in actix-web that runs an instance of a Private Key Generator (PKG). |
pg-wasm |
A library that generates Web Assembly bindings (using wasm-pack) that allows interfacing with the core library in web applications. |
pg-cli |
A command-line (client) utility that encrypts and decrypts files. |
Authentication providers
PostGuard uses Yivi, a privacy-friendly identity platform, to authenticate these identities. These identities are stored on the users phone in the Yivi app in the form of uniquely identifying attributes. These attributes can freely and selectively be disclosed by the user to any party, but only with explicit consent of the user. Eventhough PostGuard uses Yivi, other authentication modules could easily be intregrated.
Session flow
A typical PostGuard session can be depicted as follows. The red actions require user interaction. All other actions are automatic.
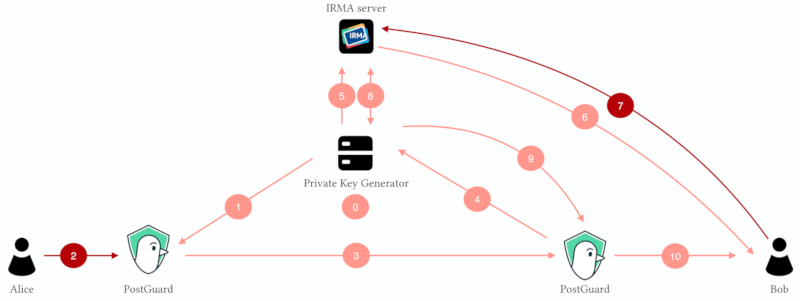
- The PKG generates a public/private master key pair.
- Alice's client retrieves the public master key from the PKG.
- Alice uses the public master key and Bob's identity to encrypt a message.
- Alice's client sends the ciphertext to Bob via a possibly untrusted channel/cloud storage.
- Bob's client asks for a key to decrypt the ciphertext.
- The PKG starts an authentication session at the Yivi server.
- Bob is asked to reveal his identity, using a QR code.
- Bob reveals his identity.
- The Yivi server sends the authentication results to the PKG.
- The PKG issues a key for Bob's identity.
- Bob's client decrypts the ciphertext using his just obtained key.
Funding
Development of PostGuard was initially funded by the Next Generation Internet initiative (NGI0) and NLnet. The project is currently funded by a 4-year project from NWO under the name "Encryption 4 All".
Dependencies
~6–19MB
~276K SLoC